Showing posts with label hackers. Show all posts
Look In to | Helping Hackers Steal Your Data
Editor’s note: This article is contributed by Lenin VJ Nair. Lenin used to work with the DSL Internet department of AT&T for two years, and now runs an online technology magazine called Blue Bugle targeted at latest smartphones, tablets, desktops, and web technologies. You can find him onTwitter and Facebook.
We know hackers are all around us, and that’s why we are extra paranoid about our online accounts and passwords. In fact, in the current web environment, hacking is not a direct job targeting yourGmail or your Facebook account. It is a controlled chain reaction involving all your linked accounts. From one service the hacker gets important security information about another; then he ‘hacks’ that account, and so on.
We however think that big companies and tech geeks are immune to hacking, don’t we? But is it really the case?
No One Is Safe
Wired writer, Mat Honan’s account was hacked last year, and the hackers (identified as Clan Vv3 and Phobia) took control over his Gmail account and terminated it.
From there, they took over his Twitter and Amazon accounts and then his Apple account, and eventually deleted everything from his Apple iCloud service. The painful truth is that Mat Honan had helped pave the way to this elaborate scam. As an example, since tech blog Gizmodo’s Twitter account was linked to Mat Honan’s, the hackers got access and took liberties with the Twitter account too.
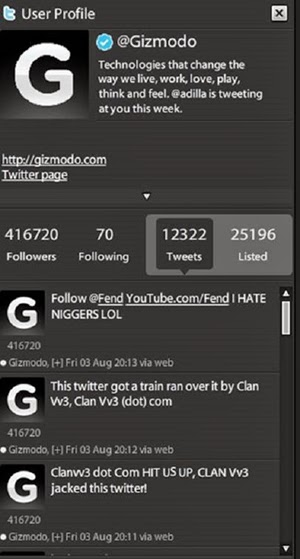
(Image source: Dailydot.com)
In another story, Labnol’s Amit Agarwal was also subjected to a Facebook account hack, which was not successful as the author immediately took action and locked the account.
No one is immune to hacking. It can happen to anybody, and when it does, there is no point regretting it. You really have to know what sort of security you have on all your web services, and how you can better manage them.
How You Are Helping Hackers
Here, we will see some obvious things you can do to make yourself immune to hacking.
Here, we will see some obvious things you can do to make yourself immune to hacking.
1. Facebook Profiles
As the largest social network, Facebook profile is the first thing you need to secure. Go, check it out from the outside. Log out of your Facebook then look your account up, from an outsider’s point of view.
If your Facebook profile shows too much information, you will likely victimize yourself. Check out this particular user’s public Facebook profile, specifically doctored for this article (that means it’s not real. I have only masked the email address, as we need an actual email address to do this. ).
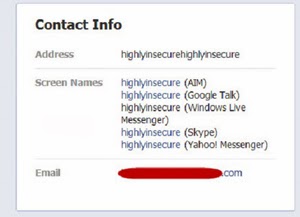
This particular profile lists apparently innocuous information, like the IM screen names on Google Talk, AOL (AIM), Yahoo, etc. What you probably forgot, but a hacker knows and takes very seriously, is that a screen name is actually your email address. For instance, highlyinsecure@gmail.com is an email address owned by this particular user. It is wide in the open for everybody to see.
It is good to share your email address with the people you know. Otherwise, it is better not to share it at all.
2. Account Recovery Hack On Facebook
Let’s do an experiment. Pretend you forgot your password, then go into Facebook. Facebook may ask you for your email address, your user name or your mobile number. You can provide that information, and it will send you an email with instructions to reset your password.
Previously, there was a method employed by Facebook to reset the password, and that method had your trusted friends involved for the purpose. It sounds foolproof unless you accept a lot of friend requests on Facebook. Picture this: You get a friend request from a few people that you don’t know. If you are the friendly type, you’d probably accept those four requests.
One thing you don’t know is that those accounts may be operated by one or more hackers. What they will do is simply raise a password reset request on your account, and select three of those four accounts as your "trusted friends". Facebook emails security codes to those trusted accounts, and boom, the hacker takes over your Facebook account. If you have problems with that, then you should take a look at this post of mine to figure out what to do.
Fortunately, Facebook no longer uses this particular method. It also doesn’t rely on security questions any more. Right now, in order to gather access to a Facebook account, the only way is by securing access to the original email address.
Hence, a hacker needs access to your email account to get into your Facebook account.
2. Email Security
Which email service are you using? Depending on that, the security differs. If it is Gmail, I would extremely recommend that you start using the two-factor authentication.
Here are the steps:
1. Go to your Google Account settings (not Gmail settings) and go to the Security option.
2. You will see 2-Step verification option. Turn the status ON.

3. Add your phone number. Select to receive the codes by text messages or voice call.
4. Enter the code received to verify your account. Make sure you update the records if you change your phone number.
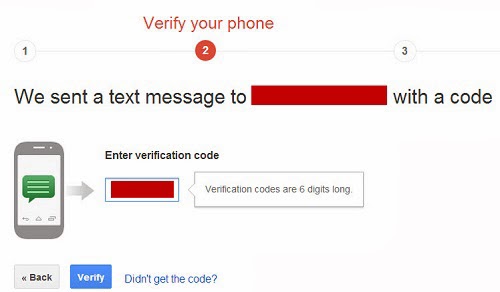
Another important thing on Gmail is notifications about suspicious login attempts. You can opt for email as well as phone notifications if any suspicious login is detected on your Gmail account.
The Truth About Security Questions
Google has a security question that you need to set. Make sure it is set properly. While I was working with email security for AT&T, I have encountered elderly customers answering security questions very truthfully. Even though I took time in explaining to them what a security question is and why they needn’t submit the true answer all the time, most of them did not quite understand it.
Most people don’t realize the fact that a security question answer works exactly like a password, only less secure depending on how you through your information about. Talking about your pet Rover on Facebook a lot then setting it it as your Security question maybe risking it a little. Anybody can access your account, whether or not they know the password, just by making educated guess about your preferences, which would work if you are truthful with your security questions.
3. Website Owners, Beware!
If you get into the Whois database of my website, you will get to see an email address that I own. It is right there, publicly available in the open. It is an email address I still use. However, it is completely detached from my website or any other important service that I use. And there is a good reason why.
In effect, even if you know it, you will not be able to access my website, my Facebook page, or my Twitter account because none of them uses that particular email address.
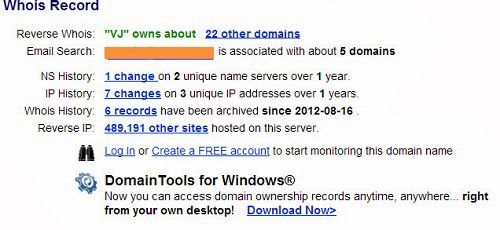
You, as a website owner, should secure the information you share with the world. You can easily do this if you spend a little more money with your hosting provider to mask the website’s registration information. All hosting providers make it available to their customers at a small fee, but I didn’t do it simply because I cannot afford it.
Whois database gives a hacker not only an email address, but also a physical address, details of the hosting provider, name of the organization, a phone number, etc. An expert hacker looking through this database can easily get valuable info about your hosting account. If you have low security on the email address and website, you will easily subject yourself to attacks.
4. Customer Service
If you are using the customer service option to reset your password for your email, the customer service executive may ask you your security question. Within AT&T, we used to use security questions to verify customers, questions like "Who is your favorite hero?", and answers like "Batman".
Not only that, we were authorized to provide the first letter of the answer if the customer gets it wrong the first time. A hacker can easily fake it since the random operator cannot identify the voice of the caller, and is supposed to divulge a password if the caller gives the correct answer.
In other companies also, the customer service executives can easily give a hacker your password or other important information from your account (such as your birth date) based on a trivial verification process. The information obtained from this call, may be used to verify an account in another service, and the chain goes on. It is very important to know what services you are using and how you can successfully verify yourself with the customer care department of those services.
Conclusion
Today, we are using not a few but a huge number of online services to get things done. Social media and email may be somewhat unimportant to some of you but what about online banking? It goes without saying how important it is to secure your banking account. I know there are elderly people who have no idea what Phishing is or how to create a good password.
A painful truth is that the security experts working in the companies you trust with your information actually expect you to know a little more about security. A security expert barely stresses the importance of these things. They cannot explain how to make a good password to each and every customer while trying to come up with better and more powerful ways to keep your online accounts safe. It is hence the responsibility of each and every one of us to know more about security in today’s world and act intelligently.